You've erased the snoopiest of the snoopy apps, decided out of tracking whenever possible, and taken all of the other preventative measures the popular how-to personal privacy guides have actually informed you to. The bad news-- and you may desire to sit down for this-- is that none of those actions are sufficient to be totally complimentary of trackers.
Android Phones Still Track You When You Opt-Out
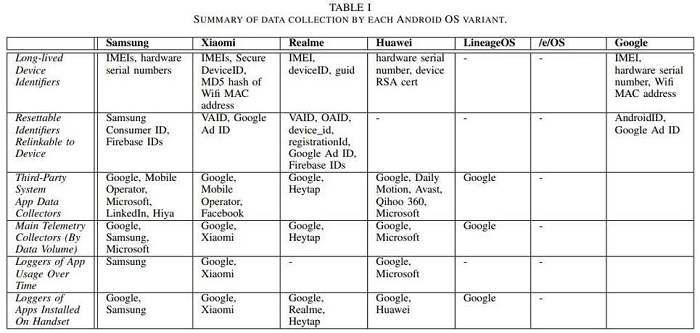
Or a minimum of, that's the thrust of a brand-new paper from scientists at Trinity College in Dublin who had a look at the data-sharing routines of some popular variations of Android's OS, consisting of those established by Samsung, Xiaomi, and Huawei. According to the scientists, "with little setup" right out of the package and when left sitting idle, these gadgets would ceaselessly pingback gadget information to the OS's designers and a variety of chosen 3rd parties. And what's even worse is that there's typically no other way to pull out of this data-pinging, even if users wish to.
These are apps that come pre-installed by the hardware producer on a particular gadget in order to provide a specific kind of performance: an electronic camera or messages app are examples. Android usually packages these apps into what's understood as the gadget's "check out just memory" (ROM), which indicates you can't erase or customize these apps without, well, rooting your gadget.
Even though there's a great opportunity you'll never ever open LinkedIn for any factor, that hard-coded app is continuously pinging back to Microsoft's servers with information about your gadget. In this case, it's so-called "telemetry information," which consists of information like your gadget's special identifier, and the number of Microsoft apps you have actually set up on your phone.
When it comes to the hard-coded apps that you may really open every once in a while, much more information gets sent out with every interaction. The scientists captured Samsung Pass, for instance, sharing information like timestamps detailing when you were utilizing the app, and for how long, with Google Analytics. Ditto for Samsung's Game Launcher, and each time you bring up Samsung's virtual assistant, Bixby.
Huawei gadgets were captured doing the very same. And on gadgets where Microsoft's SwiftKey came pre-installed, logs detailing every time the keyboard was utilized in another app or in other places on the gadget were shared with Microsoft, rather.
We've hardly scratched the surface here when it pertains to what each app is doing on every gadget these scientists checked out, which is why you need to have a look at the paper or, even better, take a look at our convenient guide on spying on Android's data-sharing practices yourself. For the many parts, you're going to see information being shared that looks quite, well, boring: occasion logs, information about your gadget's hardware (like design and screen size), along with some sort of identifier, like a phone's hardware serial number and mobile advertisement identifier, or "AdID.".
By themselves, none of these information points can determine your phone as distinctively yours, however, taken together, they form a special "fingerprint" that can be utilized to track your gadget, even if you attempt to pull out. The scientists mention that while Android's marketing ID is technically resettable, the truth that apps are generally getting it bundled with more irreversible identifiers suggests that these apps-- and whatever 3rd parties they're dealing with-- will understand who you are anyhow. The scientists discovered this held true with a few of the other resettable IDs used by Samsung, Xiaomi, Realme, and Huawei.
To its credit, Google does have a couple of designer guidelines implied to prevent especially intrusive apps. It informs devs that they can't link a gadget's distinct advertisement ID with something more consistent (like that gadget's IMEI, for instance) for any sort of ad-related function. And while analytics service providers are permitted to do that connecting, they can just do it with a user's "specific approval.".
" If reset, a brand-new marketing identifier need to not be linked to a previous marketing identifier or information originated from a previous marketing identifier without the specific authorization of the user," Google describes on a different page detailing these dev policies. "You need to follow a user's 'Opt-out of Interest-based Advertising' or 'Opt out of Ads Personalization setting. If a user has actually allowed this setting, you might not utilize the marketing identifier for producing user profiles for marketing functions or for targeting users with customized marketing.".
It's worth mentioning that Google puts no guidelines on whether designers can gather this info, simply what they're enabled to do with it after it's gathered. And since these are pre-installed apps that are typically stuck on your phone, the scientists discovered that they were typically permitted to side-step users' personal privacy-specific opt-out settings by simply ... downing along in the background, no matter whether that user opened them. And without any simple method to erase them, that information collection's going to continue occurring (and keep occurring) till that phone's owner either gets imaginative with rooting or tosses their gadget into the ocean.
Google, when inquired about this un-opt-out-able information collection by the folks over at BleepingComputer, reacted that this is merely "how contemporary mobile phones work":.
As described in our Google Play Services Help Center short article, this information is necessary for core gadget services such as push notices and software application updates throughout a varied community of gadgets and software application developments. Google Play services utilize information on licensed Android gadgets to support core gadget functions. Collection of restricted fundamental details, such as a gadget's IMEI, is essential to provide crucial updates dependably throughout Android apps and gadgets.
As part of the research study, the group looked into a gadget equipped with/ e/OS, a privacy-focused open-source operating system that's been pitched as a "deGoogled" variation of Android. And would not you understand it, when these gadgets were left idle, they sent out "no info to Google or other 3rd celebrations," and "basically no info" to/ e/'s devs themselves.
Simply put, this previously mentioned tracking hellscape is plainly just unavoidable if you seem like Google's existence on your phones is inescapable, too. Let's be sincere here-- it sort of is for the majority of Android users. What's a Samsung user to do, besides, y' understand, get tracked?
So-called "confidential" information, like your gadget's hardware specifications or advertisement ID, normally falls through the fractures in these laws, even though they can normally be utilized to determine you regardless. And if we can't effectively require an overhaul of our nation's personal privacy laws, then possibly one of the lots of enormous antitrust fits Google's looking down right now will ultimately get the business to put a cap on some of these intrusive practices.













COMMENTS